- Solution
- Products
- Brand
- Support
- Sustainability Strategy
- Foreword
- Corporate Governance Operation
- Business Partnership
- Create Shared Value
- Sustainable Environment
- ESG Report
- Stakeholder Questionnaire
- How to Buy

Information Security Policy
In the era of information explosion, Ace Pillar attaches great importance to the issue of information security. To ensure corporate information security, relevant information operating guidelines are formulated in accordance with the ISO9001 international standard to avoid risks caused by information leakage and ensure the confidentiality, integrity, availability and legality of corporate assets, and avoid internal and external intentional or accidental threats to avoid risks and achieve sustainable corporate management.
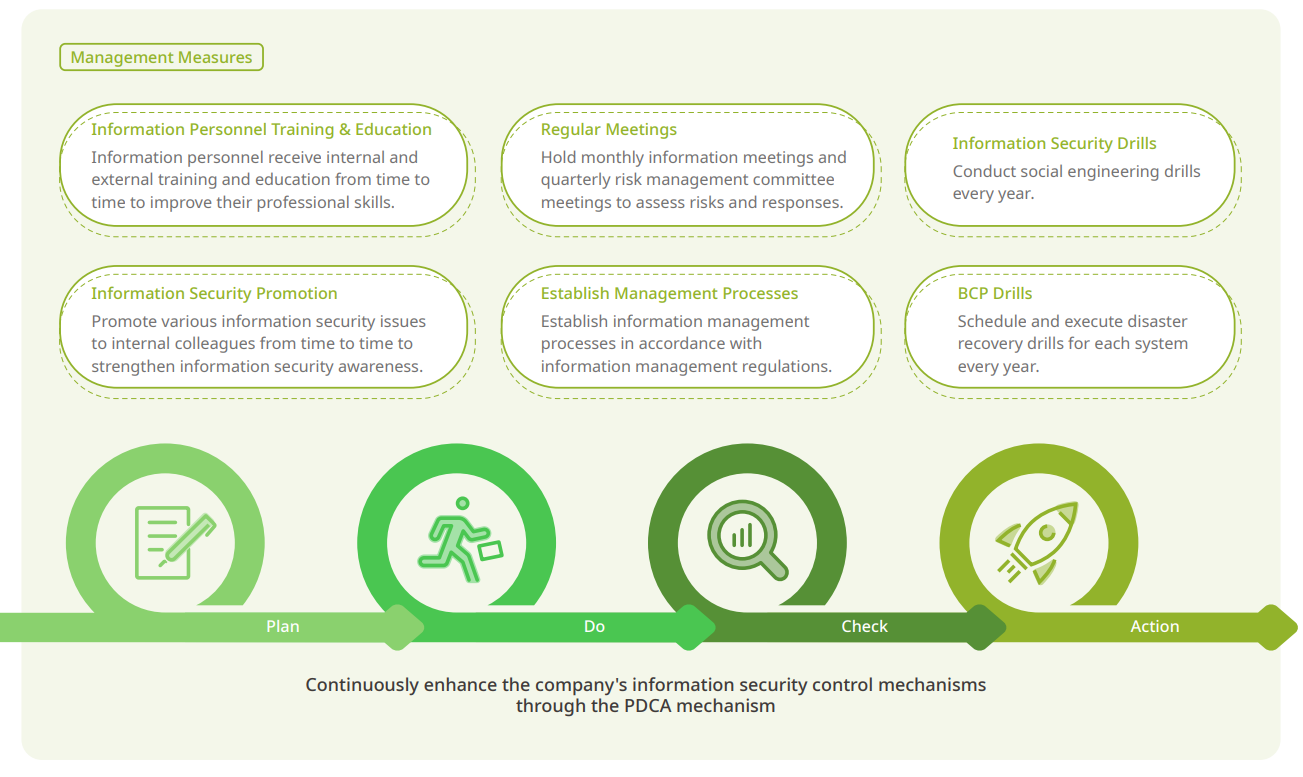
Information Security Management
Through the establishment of an information security management system, Ace Pillar implements information security policies, protects customer data and company intellectual property, strengthens the response capabilities of information security incidents, and achieves information security policy measurement indicators, as well as meets the expectations of stakeholders for the company.
The Information Department leads the promotion of the company's information security, and effectively protects the security of the company's intellectual property through the specifications and tools of information assets, and enhances colleagues' information security awareness.
Account Security Control
- Each internal employee has their own network account and password, and accounts are promptly closed when employees leave the company.
- Access to information is granted according to job duties and levels, and employee system access is regularly reviewed annually.
- The passwords of system accounts are required to meet complexity and length requirements, and are regularly forced to be updated.
- Enhance user identity verification.
System Security Control
- Regularly perform vulnerability scanning on various systems, and irregularly detect whether the firewall has been invaded to ensure the security of the company's systems.
- The data used internally by the company is backed up according to the 3 (sets of backup data), 2 (types of different storage media), 1 (off-site or cloud) principle to ensure secure data storage.
- Regularly update relevant antivirus software and firewall versions.
Measures for Major Information Security Incidents
In October 2023, Ace Pillar discovered that the system was invaded by hackers and quickly activated emergency measures, cooperating with information security companies to find the cause and strengthen vulnerabilities. The system was rebuilt within 3 days to restore daily operations. Through this information security incident, network security management practices were adjusted to reduce the chance of external detection and intrusion, and various information security prevention measures were introduced to strengthen the security protection of information systems. Avoiding the recurrence of incidents and reducing the company's losses.
- Solution
- Products
- Brand
- Support
- Sustainability Strategy
- Foreword
- Corporate Governance Operation
- Business Partnership
- Create Shared Value
- Sustainable Environment
- ESG Report
- Stakeholder Questionnaire
- How to Buy
- About
- Support
- Others
- ACE PILLAR Subsidiary Website